Hackers 1st Step: Information Gathering

What is Information Gathering
Gathering information is the initial stage where a hacker tries to obtain information about the victim. Hackers utilize different sources and tools to extract more information, and those snippets of data will get value for a hacker to get into your organization or your gadgets.
Objectives of information gathering in cybersecurity
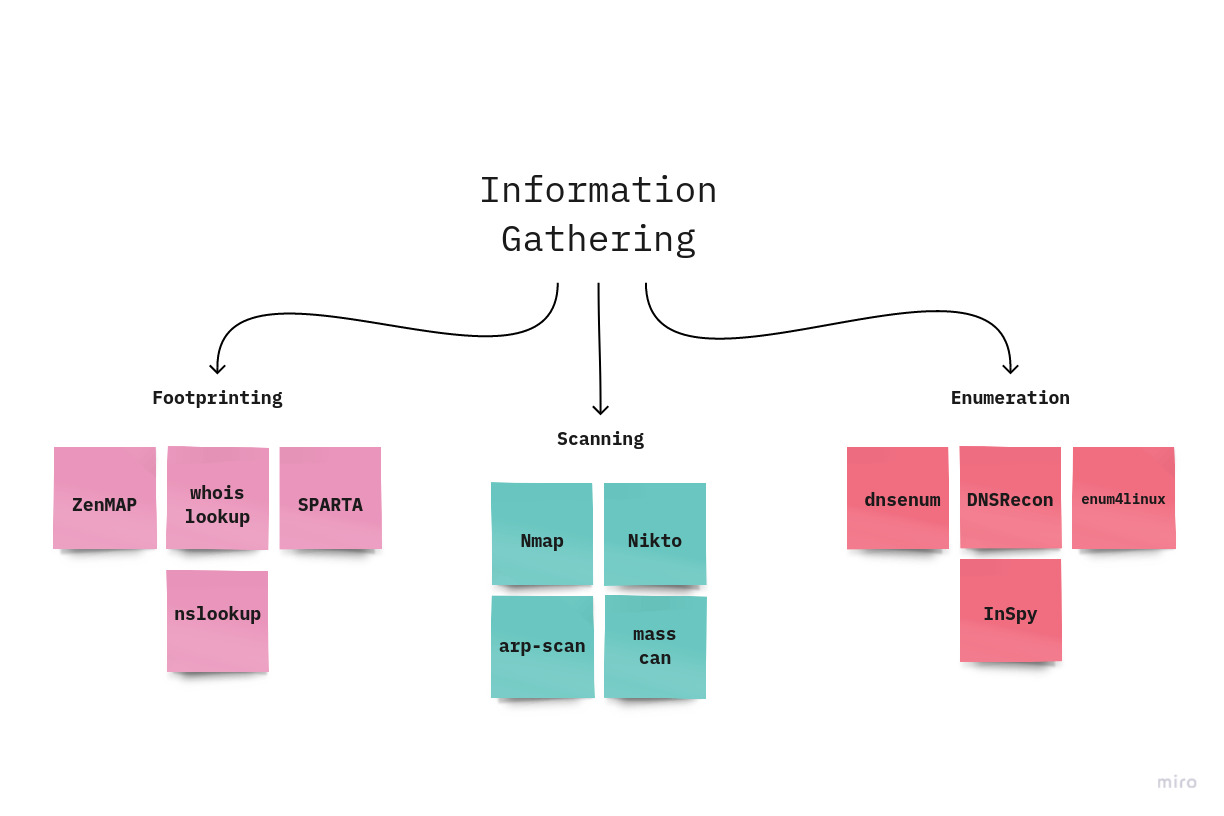
These are the two sorts of information assortment focuses on that are regularly engaged with the information gathering measure:
- Footprinting & Scanning : This includes public, private, and associated domain names, SSL certificates, network hosts, Open Ports, public and private IP blocks, routing tables, TCP and UDP running services, and more.
- Enumeration : This includes OS hostnames, user enumeration, system banners, system groups, OS type fingerprinting, etc.
While there is a lot to cover, you will find out about it by investigating the most famous methods utilized during this stage.
Information gathering techniques :
Commonly, hackers use an assortment of strategies and tools to acquire this valuable data for their targets, for example, data from social media and online job profile locales to use toward a data gathering target.
Let's take a look at the top strategies used to accumulate data about any target.
Social engineering: It includes in-person chats, phone conversations, and email spoofing attacks. All these methods typically involve psychological manipulation of people's activities or splitting confidential information, which is relevant to get all information about the target.
Search engines : Web crawlers can be used to obtain information about all, including companies, individuals, and services.
Social networks : Facebook, Twitter, LinkedIn, and other interpersonal organizations are vast wellsprings of data for building profiles, unusually while focusing on somebody.
Domain names : These are enrolled by organizations, governments, public and private organizations, and individuals. Subsequently, when you need to observe somebody, they are an extraordinary beginning stage. These can be easily discoverable by inspecting domain name information of private information, associated domains, projects, services, and technologies.
Internet servers : An Authoritative DNS server is an incredible wellspring of data, as they frequently incorporate each surface point uncovered on the Internet - which means an immediate connection to related administrations, for example, HTTP, email, and so forth.
Information gathering tools:
There are hundreds of Information Gathering tools available out there on the Internet as open-source software. But we will list out the most used and popular tools, Which will help you during the Information Gathering process.
Nmap : It is known as a network mapping tool. This tool always comes first in the mind of every hacker when it comes to gathering information. You can use this tool for various purposes such as port and service scanning and DNS enumeration.
Sublist3r : This is the best subdomain enumeration tool, which will help you to create a virtual subdomain map of any website within a second. This can be used to carry out a brute force subdomain search attack with a wordlist, using Google Dork and other search engines such as Baidu, Ask, Yahoo, or Bing.
Bettercap : It is known as the Swiss Army Knife for networking, used mostly for network recon and information gathering, especially for WiFi, Bluetooth low energy devices, and Ethernet networks.
Th3inspector : This infosec tool will empower you to check a wide range of site-related data, for example, page information, telephone numbers, HTTP and IP locations of email servers, perform a WHOIS query, bypass Cloudflare proxy, check the age of your domain name. Serve as remote active services, subdomain mapping, and even CMS detector.
WHOIS : This tool can fetch domain and IP-related information, including technology and administrator names, telephone numbers, addresses, countries, DNS servers, and more.
Dig : This tool is used to find all data about DNS records, Dig is the best tool that will help you to enumerate Domains, it can find all records of a registered domain such as A, NS, TXT, or CNAME records.
Web Archive: It is a non-profit, public digital library founded in the year 1995. Its mission is to provide “universal access to all knowledge”. The Archive is an activist association that is free and open to the Internet.
Currently, the archive stores free, public access to:
-
410 billion web pages
-
20 million books and texts
-
4.5 million audio recordings and 180,000 live concerts
-
4 million videos and 1.6 million television news programs
-
3 million pictures
-
200,000 software programs
Registered users can upload their content to the archive. The web.archive.org is a digital archive of the World Wide Web. Since its dispatch in 2001, more than 452 billion pages have been added to the archive.
A user can enter a URL to see and access the past website of any site contained in the archive, regardless of whether that webpage doesn't exist on the web(live).
Google Hacking: Google hacking is the utilization of web crawlers, for example, Google to distinguish security weaknesses on the Internet. Two sorts of vulnerabilities are regularly found on the web one is programming weaknesses and misconfigurations(errors).
And the fact that some complex intruders focus on a particular framework and attempt to find weaknesses that will permit them access. Most of the intruders start finding particular programming vulnerability or basic client misconfiguration that they already know how to misuse, and simply attempt to look or scan for systems that have this vulnerability.
With the help of google, an attacker can gain access to webcams with public access, gain access to sensitive Gdrives and Folders, gain access to Drive documents with sensitive information i.e passwords.
Recon-NG: Recon-NG is a web reconnaissance framework written in Python programming. It's a complete automation modular framework, database interactions, interactive assistance, Recon-ng is an incredible TUI tool in which reconnaissance can be led rapidly and adequately.
While using it you will feel similar to the Metasploit Framework, but it is quite different. It is exclusively designed for web-based reconnaissance.
Shodan: Shodan is the web crawler for everything on the web. While Google and other web crawlers only list the web (index), shodan list (index) everything such as - webcams, hydro medical facilities sources, boats, medical and medical type equipment, traffic signals, wind turbines, license records, Smart TV, and devices information, AC, anything, and everything. It contains all that is associated with the web.
Pastebin: Pastebin is a site that permits clients to share texts or code through open posts called "pastes". The site at present has 17 million unique monthly visitors.
It mainly supports inoffensive content sharing, additionally turns into a well-known platform for hacking and illegal operations. For example, breached data and other sensitive information, software vulnerabilities, illegal access to a website, dark web links, copyrighted information of banks, credit card, or financial information, pornographic information, etc.
These are examples of how pastes sites are utilized by blackhats. Pastebin is especially easy to understand, one can post lots of text files, it doesn't need client enrollment, it permits unknown posting if the client has a VPN.
It depends on users reporting to a paste, which means that non-compliant pastes are not generally flagged as spam or taken out right away immediately. This permits blackhat hackers to effectively and namelessly access information in an open area.
HTTrack Web Site Copier: HTTrack is a free and offline site copier tool. It permits you to download the World Wide Web complete webpage from the Internet to your local drive, It retrieves all files to your computer. HTTrack organizes all the files as the structure of the parent site.
So now we know about the tools which are very useful when it comes to gathering information about any particular thing. Only the theories about the tools won't help you to understand how the thing is functioning. For a hands-on practical you can refer to the given links:
ohSINT: https://tryhackme.com/room/ohsintGoogle
Dorking: https://tryhackme.com/room/googledorking
Shodan.io: https://tryhackme.com/room/shodan
Sublist3r: https://tryhackme.com/room/rpsublist3r
networking: https://tryhackme.com/room/bpnetworking
WebScanning: https://tryhackme.com/room/bpnetworking
Nessus: https://tryhackme.com/room/rpnessus
PenTestQuiz: https://tryhackme.com/room/pentestquiz
Metasploit: https://tryhackme.com/room/rpmetasploit
MeltdownExplained: https://tryhackme.com/room/meltdownexplained
Some more OSINT challenges form HackTheBox: Breach, We have a leak and Infiltration.
Summary
Gathering data is one of the underlying advances taken during most infosec investigations, and there are numerous approaches to do it, with various methods and tools. While exploring any objective, you will be shocked how much information you get about the host.
Sometimes you get a lot of relevant information, on other occasions you come up with useless data, and, still, in other scenarios, good data and only noise will be combined. It takes time to collect all of this data, and it can be even harder to drink all the different pieces of cyberspace trails you've got, clean up all the garbage, and just get the useful and important parts ... But don't worry, that's why we are here to help you.